Introduction
KPMG’s 2020 cyber risk quantification paper provides us with valuable concepts on cyber risk quantification. I have adopted their core attack path concept for ransomware and built a Monte Carlo simulation. The model works on three interlinked components:
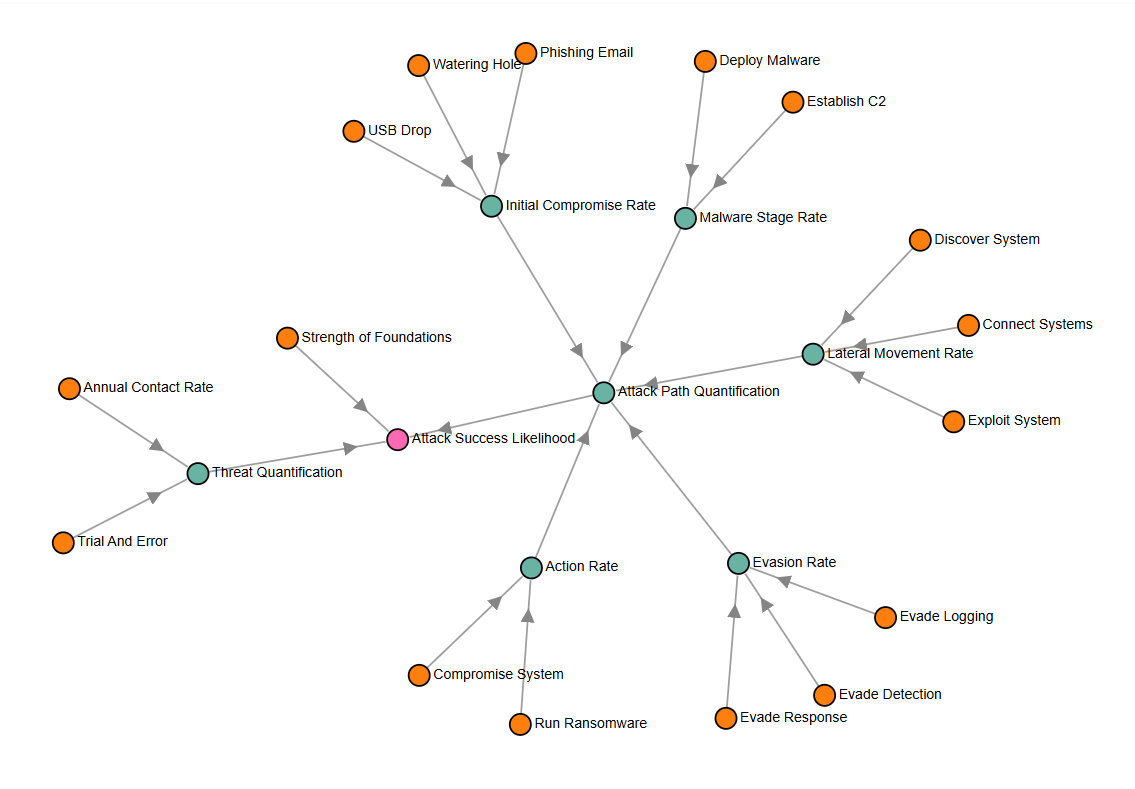
1. Threat Quantification (Contact Rate × Learning)
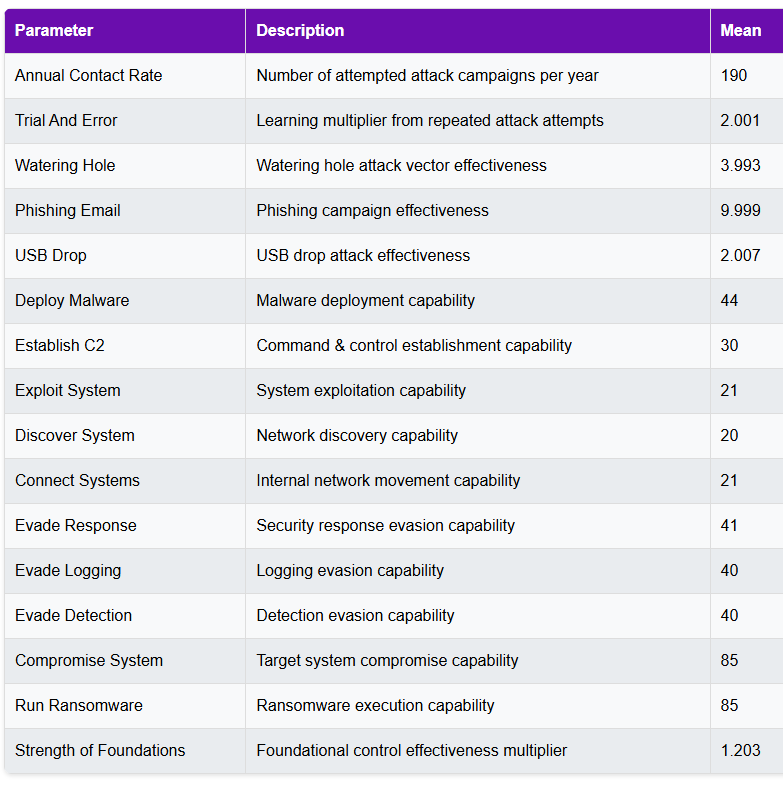
- Annual attack attempts (base rate of 190)
- Learning effect multiplier (2x) capturing attacker improvement This gives us ~380 effective attacks per year to feed into our path calculations.
2. Attack Path Success Rate
- Initial Compromise: MAX(phishing, watering hole, USB) ≈ 10%
- Malware Deployment: AND(deploy, command & control) ≈ 13%
- Lateral Movement: MAX(exploit, discover, connect) ≈ 20%
- Evasion: MAX(response, logging, detection) ≈ 40%
- Action: AND(compromise, ransomware) ≈ 70%
The use of MAX for OR nodes and multiplication for AND nodes lets us model real attack paths while keeping calculations manageable.
3. Foundation Controls
Model uses a 1.2x multiplier to represent how basic security controls enhance overall effectiveness.
Making It Real
I implemented this as a Monte Carlo simulation using:
- Parameters capturing base capabilities
- Assessments providing realistic ranges
- Expressions handling Boolean logic
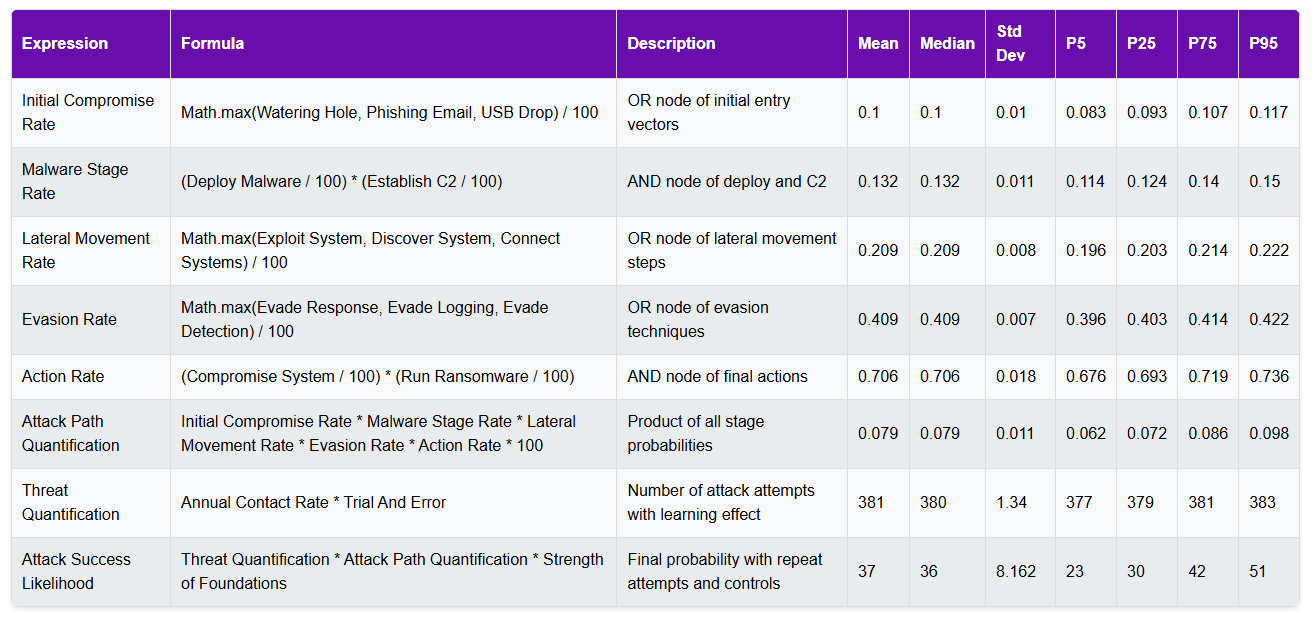
The results (37%) closely match KPMG’s predicted 33% likelihood while providing equal insight into contributing factors.
When Theory Meets Reality
Key lessons from this implementation:
- Assessment honesty matters more than mathematical precision
- AND/OR logic drastically affects which controls matter most
- Foundation multipliers capture often-overlooked basics
- Monte Carlo helps understand probability ranges, not just point estimates
Next Steps
This model demonstrates what’s possible with:
- Clear attack path definition
- Boolean probability logic
- Foundation control effects
- Practical assessment ranges
The challenge now is tuning it for specific environments while maintaining its simplicity and usability.
